Mitsubishi Heavy, NTT Develop Advanced Cyber Security Technology
Mitsubishi Heavy Industries (MHI), Nippon Telegraph and Telephone (NTT) and associated companies have commercialized InteRSePT1, a jointly developed cyber security technology for critical infrastructure control systems.
InteRSePT1 provides real-time anomaly detection and response for unknown cyber-attacks, contributing to safe and secure system operations. Sales of the system will begin in May. MHI and NTT are actively developing markets for the technology in commercial fields where continuous availability is critical, such as thermal power generation facilities and chemical plants.
In recent years measures have become necessary to counter advanced cyber-attacks that monitor the operating characteristics and control commands of the target device, and change the timing of network communication or contents of commands to cause the target device to fail.
MHI and NTT, in response to growing needs, began research and development on security technologies in March 2016. The InteRSePT prototype was completed in November that year, combining the highly reliable and safe control technologies developed by MHI for the fields of defense and space, with security control technology*7 developed by NTT.
Evaluation of the prototype and conformance testing for control systems was then conducted at Cyber Lab, MHI's facility in Tokyo for security development and testing. The functionality of InteRSePT was further improved and the range of applications broadened to include the operations and maintenance (O&M) businesses. This led to commercialization and the launch of sales.
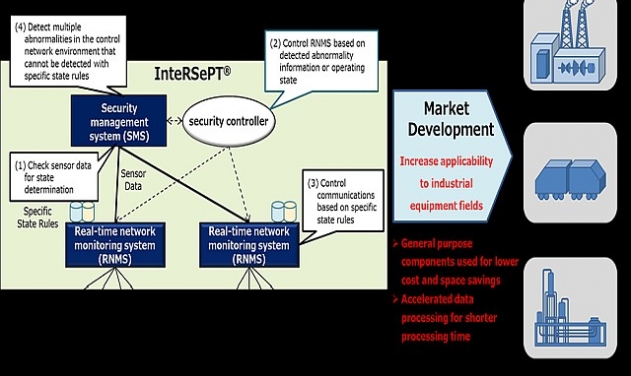
InteRSePT comprises a real-time network monitoring system (RNMS) and a security management system (SMS). The system monitors sensor information and other data flows in networks and detects cyber-attacks that exploit control commands, which are difficult to detect and respond to with conventional technology.
By changing the security remediation rules on each operating state of the target device, the system provides early detection of anomalies, and allows for a rapid response to even unknown cyber-attacks while maintaining availability.













